Overview
It is important to understand that there is no single way to use your instance. Much of how you use the instance will depend on what managed template you deployed or if you created your own template. This documentation will help you understand the basic controls in the GPU Trader interface.Stacks
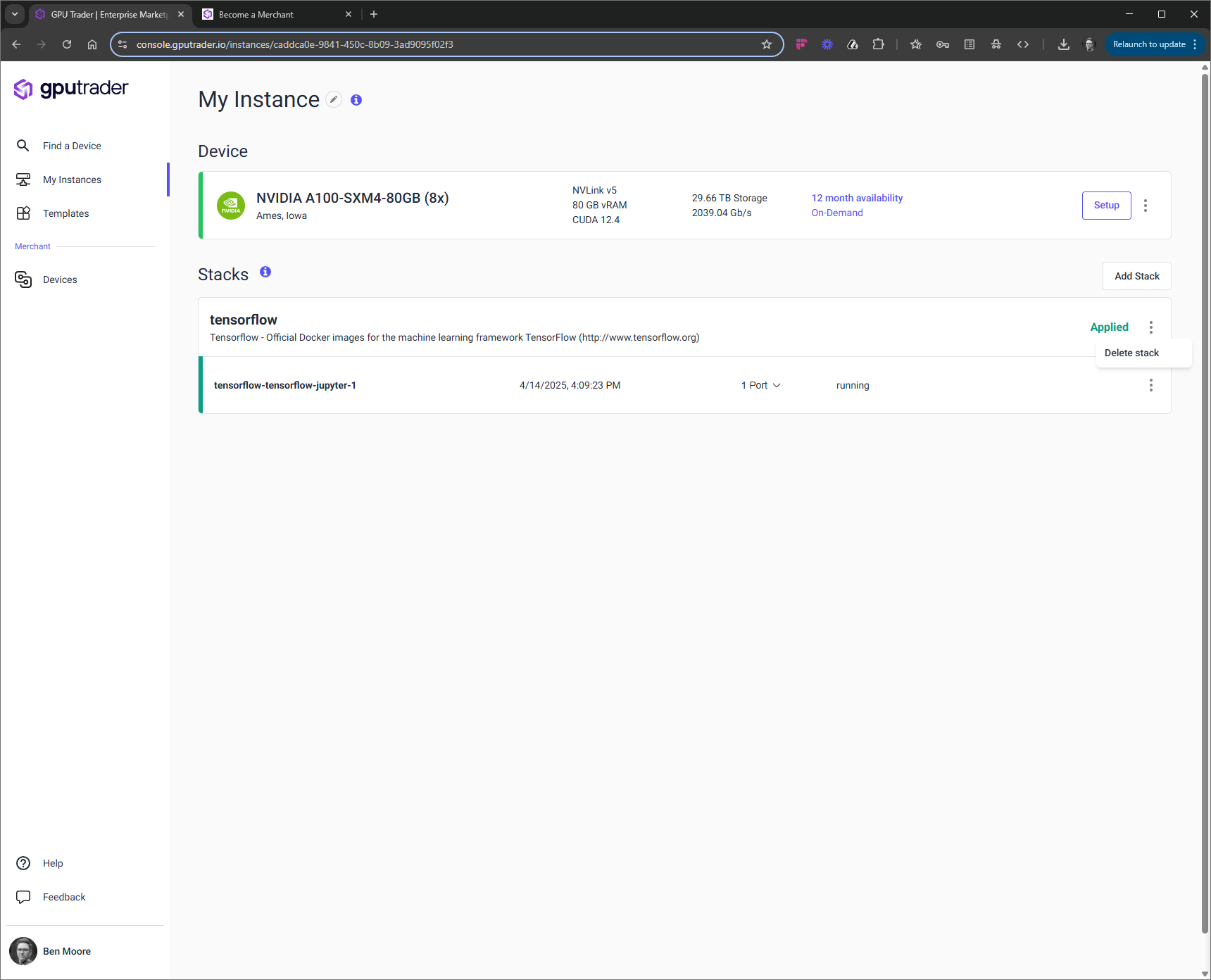
A stack in GPU Trader refers to a collection of services defined in a template (docker-compose.yml) file that is deployed on an instance. A user can have multiple stacks deployed if they have not partitioned the instance. If a user chooses to partition their instance, choosing less than the total number of cards, they will be limited to one stack.Status
Each stack has a status on the right side of its card. The most common statuses that a user will see areApplying and Applied. These statuses are normal and healthy, indicated by the green bar on the left of the stack. If the stack deployment is hanging or the resources did not deploy correctly, the user will see a red bar on the left of the card.
If you see a red status, we recommend you download the logs, delete the stack, and try deploying it again.
Connecting to your Stacks
Users can connect to their stack using a variety of methods:Web based Terminal
To use the terminal, click the ‘Kebab’ on the right and choose ‘Terminal’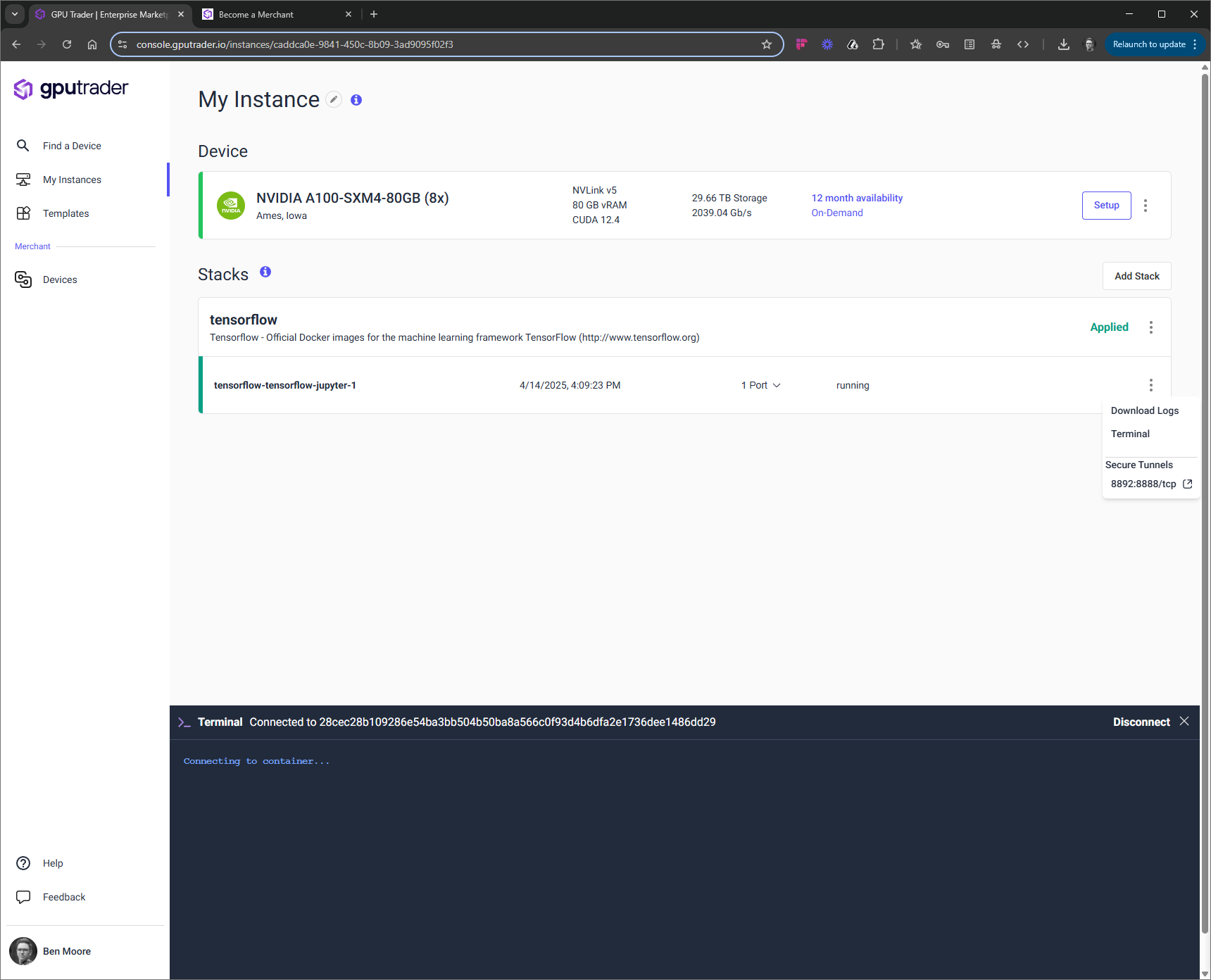
Secure Tunnel
GPU Trader includes secure point to point connections via secure reverse tunnel. To use the secure tunnel you can either (1) click the ‘Kebab’ on the right and choose the port you wish to connect to, or (2) click the ‘Port’ dropdown on the card and choose the port you wish to connect to.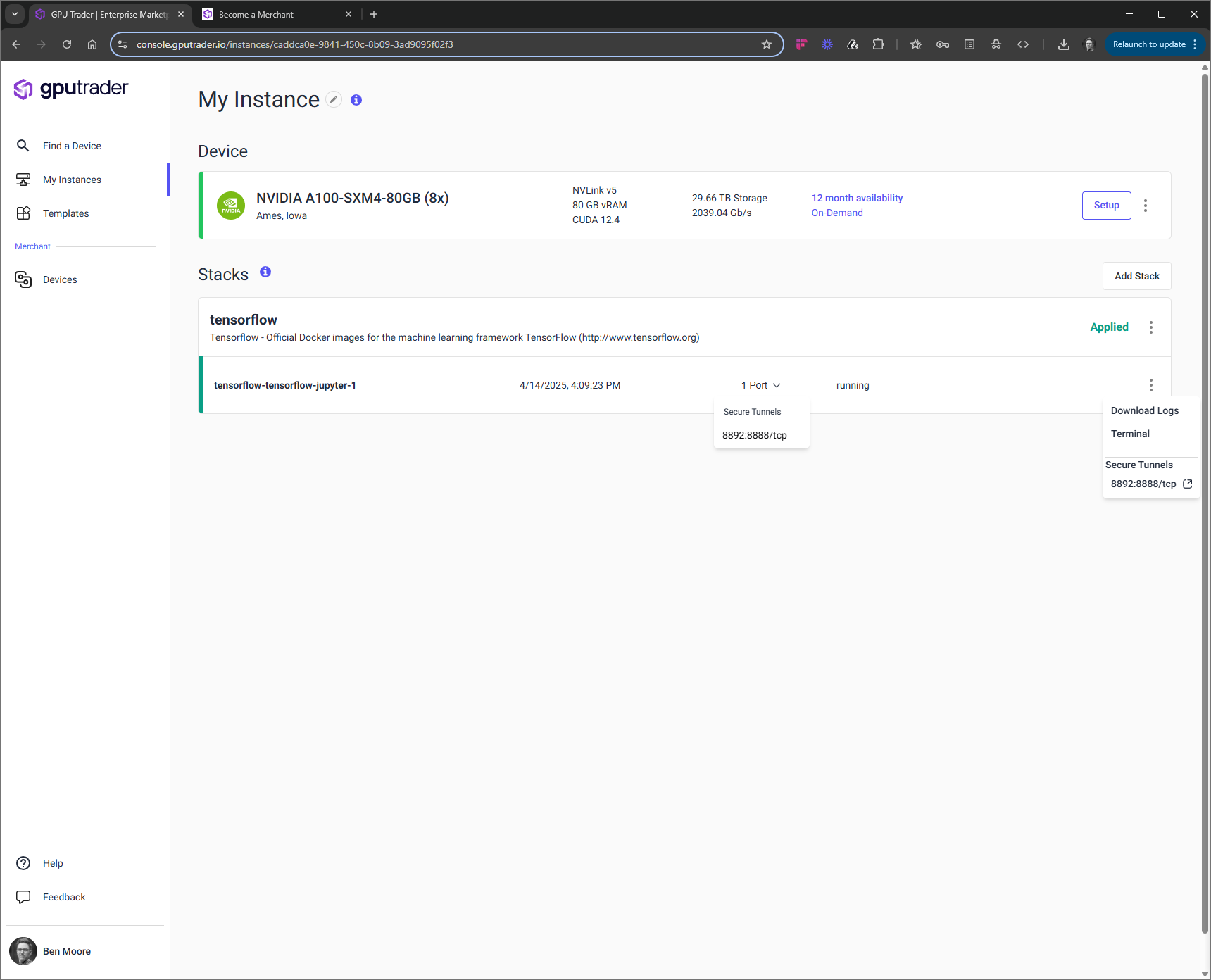
SSH
GPU Trader provides zero-trust SSH tunnel access to your deployed containers. This means no open ports on your host, no blanket network access, and no risk of leaving insecure endpoints exposed. Each connection is authorized per session and encrypted end-to-end, ensuring that only authenticated users with the correct SSH keys can access the container. Once you disconnect, the tunnel automatically shuts down—leaving nothing open behind. Read the SSH doc for more details.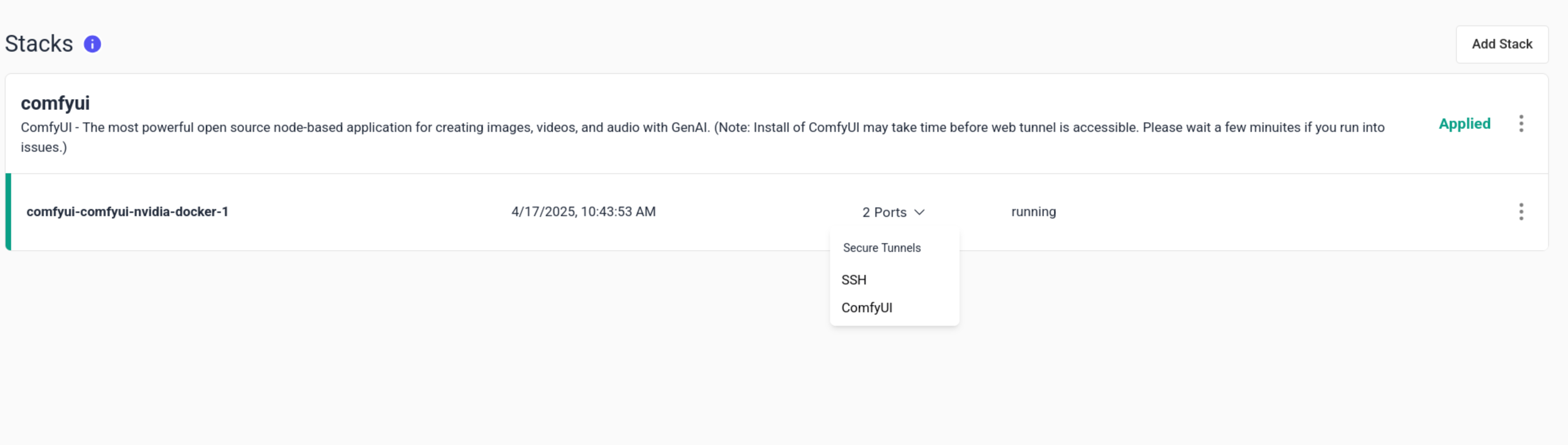
Logs
Each stack has its own log and is a useful tool for debugging when the stack does not deploy correctly. Click the ‘Kebab’ on the right of the stack and select ‘Download Logs’.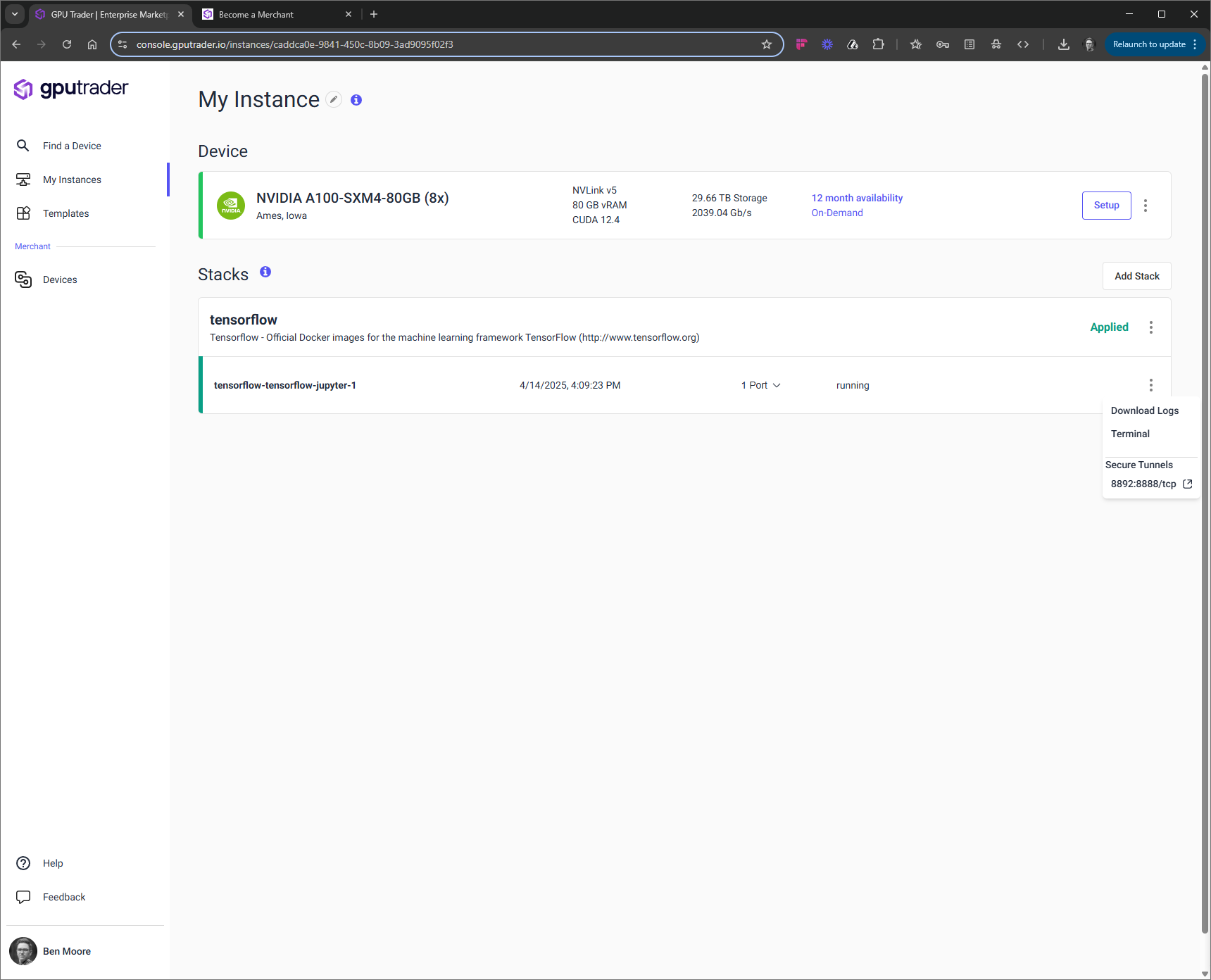
Deleting your Stack
To delete the stack select the top-level ‘Kebab’ and chose ‘Delete Stack’.